The security of web services ensures the safety of data and their inaccessibility to unauthorized persons and the ability of the application to remain operational during cyberattacks and not be infected by viruses.
A modern site is a system with a complex architecture containing on average 20 vulnerabilities exploited by attackers. 62% of sites are exposed to the medium to high-risk vulnerabilities. Both massive and APT attacks were associated with the COVID-19 topic, which grew throughout 2020. Experts note that the pandemic has contributed to accelerated digitalization. The emergence of new electronic services contributes to the intensification of crime and requires special attention from information security.
Causes of security threats
- The security of web applications depends on the quality of their program code, the system administrator’s qualifications, and the competence of all users who have access to sensitive information.
- Security threats – breaches and data leaks – can be caused by:
- Vulnerabilities of the site/application itself to a cyber attack – for example, lack of protection against brute-force passwords, the ability to inject third-party code (XSS, SQL injection, lack of protection against CSRF);
- Insufficient performance of the system or increased resource intensity of request processing, which leads to vulnerability to attacks such as “denial of service” – (D) DoS;
- Errors made by the webserver administrator – untimely software update or unsafe configuration of services;
- Ignorance or non-compliance by employees with banal safety rules.
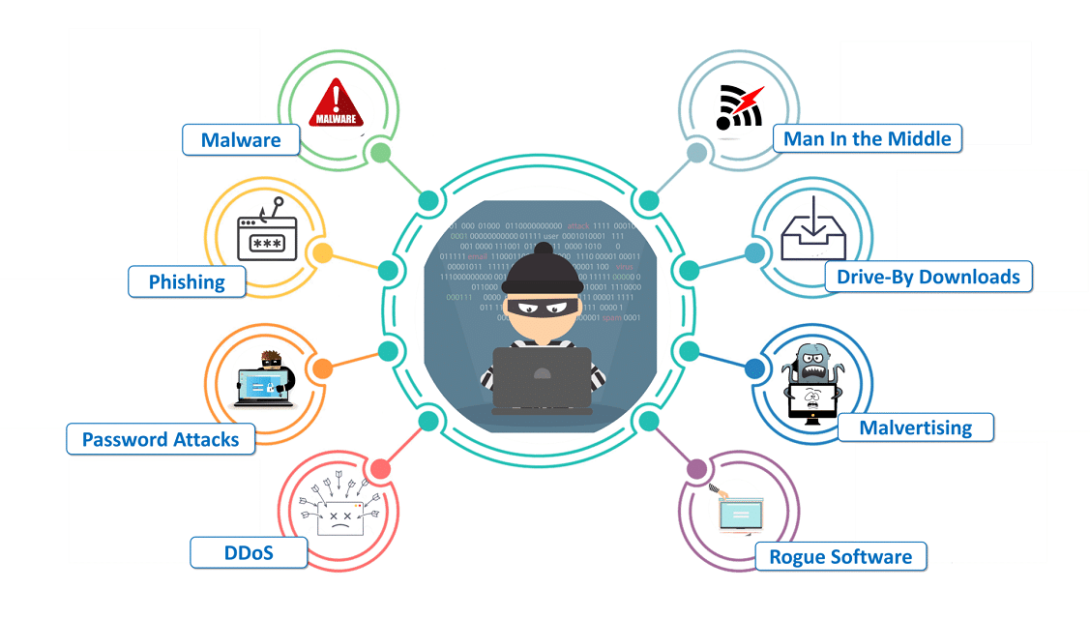
Common vulnerabilities
Let’s take a look at typical vulnerabilities that affect many web applications according to the most popular OWASP Top 10 vulnerability classification:
- Implementation
- Disadvantages of authentication
- Cross-Site Scripting (XSS)
- Disclosure of confidential data
- Insecure deserialization (merged with XXE)
- Disadvantages of access control
- Disadvantages of logging and monitoring
- Server-Side Request Forgery (SSRF
- Using components with known vulnerabilities
- Incorrect security settings
Best Practices for Preventing Potential Security Issues
- Trust the development of required security services to an experienced custom web development company. Newbies can make the application work but are unable to account for the risks of hacking and attacks.
- Server administration should be carried out regularly by a competent specialist. Most of the site infections with viruses occur because no one updates the server software, and a lot of data leaks are associated with the incorrect configuration of server services.
- Train users on the basics of information security, reduce rights to the minimum necessary for the operation and monitor sensitive information access.
- If you doubt the security of your site, then order a security audit from an independent company. The purpose of penetration testing a system can be:
- Make a list of vulnerabilities that could be exploited by an attacker and check the possibility of their implementation.
- Suggest ways to eliminate the identified vulnerabilities.
Penetration Testing Techniques
- The Open Web Application Security Project («OWASP»);
- Open Source Security Testing Methodology Manual («OSSTMM»);
- Technical Guide to Information Security Testing and Assessment (SP 800-115);
- ISACA IS auditing procedure «Security assessment-penetration testing and vulnerability analysis»;
- Penetration Testing Execution Standard («PTES»);
- A Penetration Testing Model («BSI»);
- Payment Card Industry («PCI») Data Security Standard («DSS») Guidance: PCI Information Supplement: Penetration Testing Guidance v3.2.1 June 2020.
Vulnerability identification process
Collection of information and primary analysis. Experts use open sources of information, identify infrastructure objects and environments, and build a tree of potential attacks.
Configuration test. At this stage, a check is made for the vulnerabilities of the network infrastructure, physical and virtual hosting, and the logging system.
Authentication system test. Experts test the password policy, checking how it is applied correctly, where and how account data is stored.
Authorization mechanism test. We define user roles, access control requirements, and so on.
Test of the session management mechanism, namely, checking the scope of cookies, session tokens, the presence of CSRF vulnerabilities.
Transport layer security test. We will check the security of client-server communication protocols and SSL / TLS services.
Test of processing of transmitted data. We will fuzz the client’s parameters and check the returned data from the servers, test the possibility of SQL, SMTP, SOAP, LDAP, XPath, and Frame injection.
Test of client-side security mechanisms.
Application logic test, namely, the definition of the business logic of the application and possible vectors of attacks.
Stages of work
Customer’s permission to carry out work
The customer lists all the information system components (research objects) and indicates the nodes or services that are excluded from testing. Security specialists appoint responsible persons and determine the performer’s level of awareness – Black Box, White Box, or Gray Box.
BlackBox. Classic modeling of an attacker’s actions – the performer has no information other than what he can collect himself from open sources using publicly available tools.
WhiteBox. The contractor can request and receive any information about the customer’s tested systems. This mode detects the most significant number of vulnerabilities.
GreyBox. The contractor knows only about some elements of the web infrastructure.
Platform attack.
At this stage, it is checked:
- web service platform equipment,
- Operating Systems,
- auxiliary software,
- web service architecture,
- network services and services.
It also sends requests to the customer’s network node and analyzes the responses. This activity can be captured by intrusion detection and prevention systems (IPS / IDS).
Vulnerability collection and formation of a list of potential web service ones.
Vulnerabilities known to disrupt the service are checked within a specially created test bench or at an agreed time under the supervision of a customer representative.
Checking the list of vulnerabilities
At this stage, we confirm the presence of potential vulnerabilities from the approved list. This type of work can cause a temporary increase in the load on the objects under study. After the job is done, the analysis of the results begins.
Organizations today must assume that they will ultimately be compromised. Even if an organization is equipped with state-of-the-art security products, Sensitive Data’s risk of penetration and theft cannot be eliminated. Detection automatically blocks an attack at an early stage can prevent damage. To win the battle for cybersecurity, companies need vital threat intelligence, threat prevention technologies, and consolidated security architecture.
